In most Internet of Things (IoT) deployments, it's good practice to authenticate anyone trying to access your device, typically through the Ethernet, Wi-Fi, or other network protocol. But there's a more subtle, and dangerous, way to get into your device: through a JTAG debug port. If someone gains physical access, that person can create much more havoc because JTAG takes you to the low-level heart of a board or chip, where an expert hacker can take complete low-level control of the system, even replacing firmware with a rogue code.
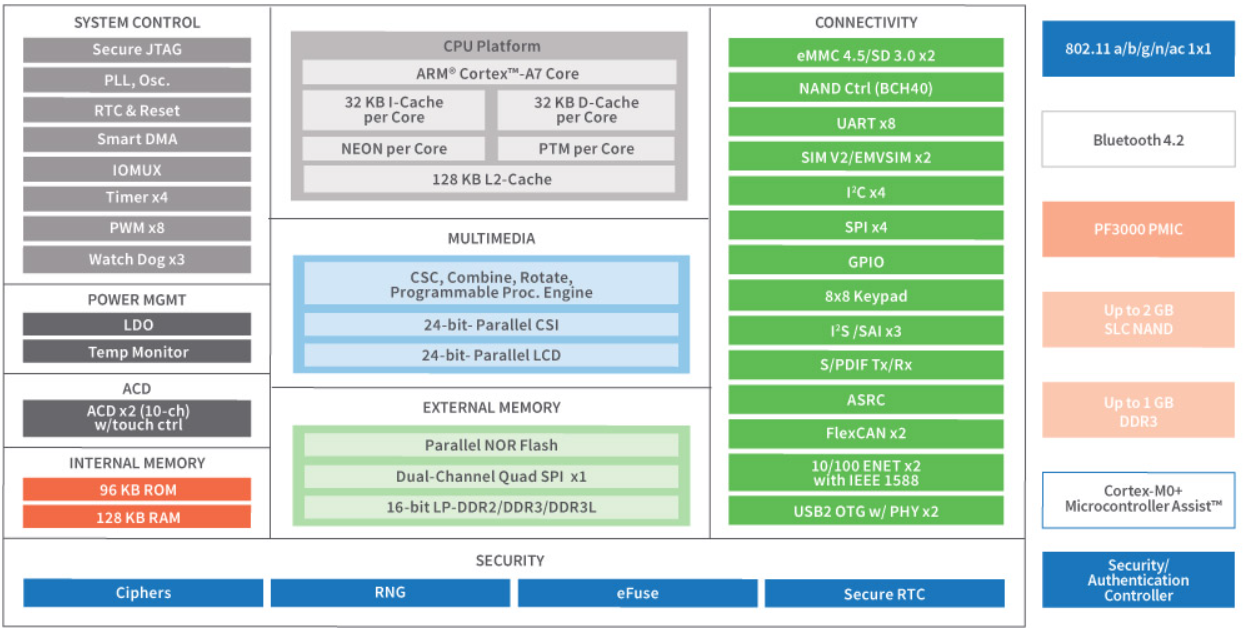
In this contributed article for Embedded Computing Design, Mike Rohrmoser explains the pluses and minuses of the use of Secure JTAG keys. Regardless of the approach you choose, Digi TrustFence® security framework includes tools for manufacturing and maintenance, including Secure JTAG.
Next Steps