DAL DMVPN Part 2 - Cisco Hub configuration
Introduction:
This is Part 2 of the DMVPN (Dynamic Multipoint VPN) Knowledge Base series, which details the configuration of DMVPN on Digi routers.
In this article, we focus on configuring the HQ router (Cisco HUB), based on the following network deployment scenario:
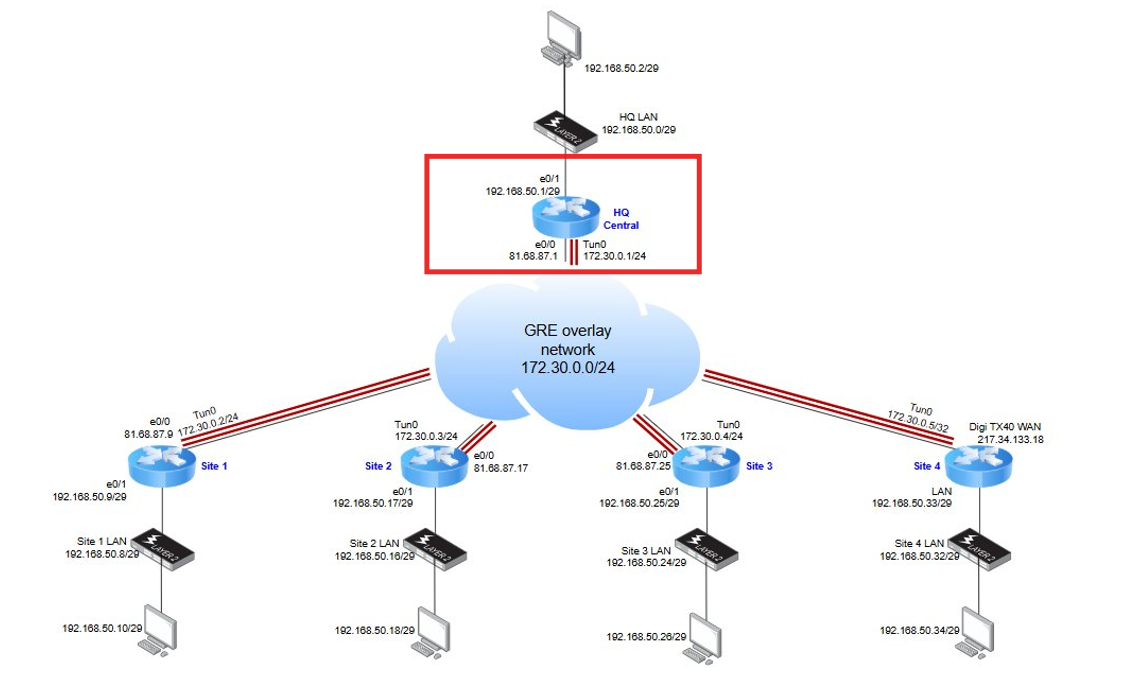
1. Network Configuration
After establishing an SSH connection to the Cisco router, the following configurations were applied:
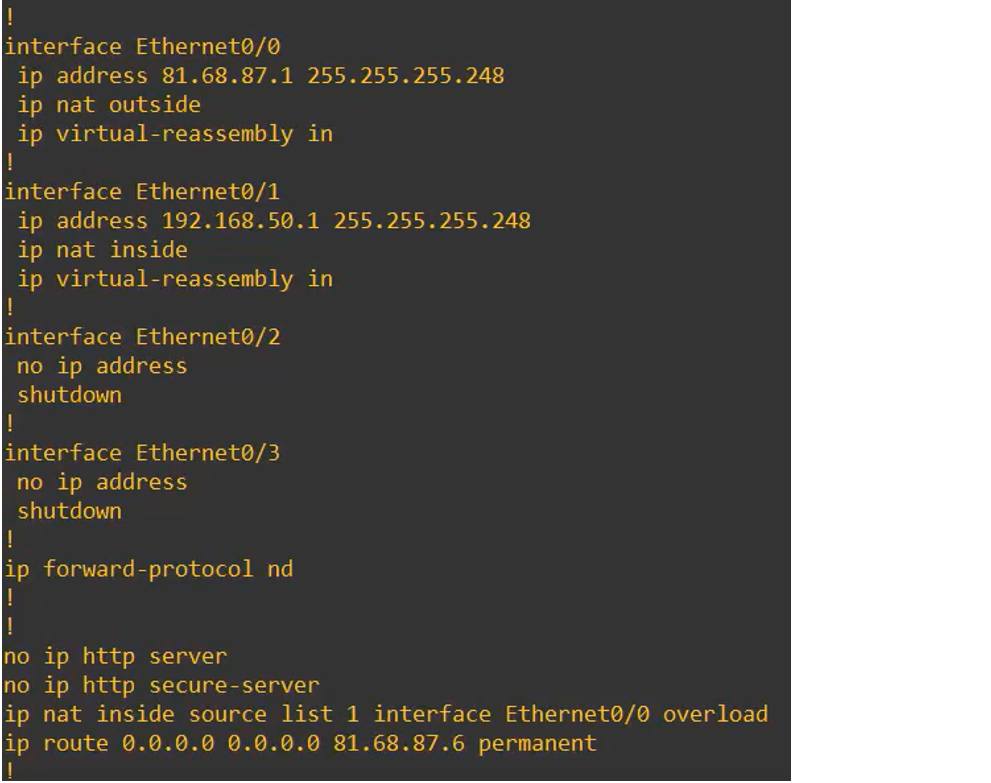
- LAN and WAN interfaces configured according to the addressing scheme outlined above
- NAT Overload enabled for internet access via the WAN interface
- Default route set to forward all outbound traffic to the upstream gateway
At this stage, the router configuration for this section appears as follows:
2. IPsec and IKEv2 Configuration
For this deployment, IKEv2 is used as the key exchange protocol. The Phase 1 and Phase 2 parameters are configured as follows:
- Phase 1 (IKEv2 Proposal):
Protocol: IKEv2
Encryption: AES 128
Integrity: SHA1
Diffie-Hellman Group: 5
Authentication Method: Pre-Shared Key
- Phase 2 (IPsec Proposal):
Encryption: AES 128
Integrity: SHA1
Perfect Forward Secrecy (PFS): None
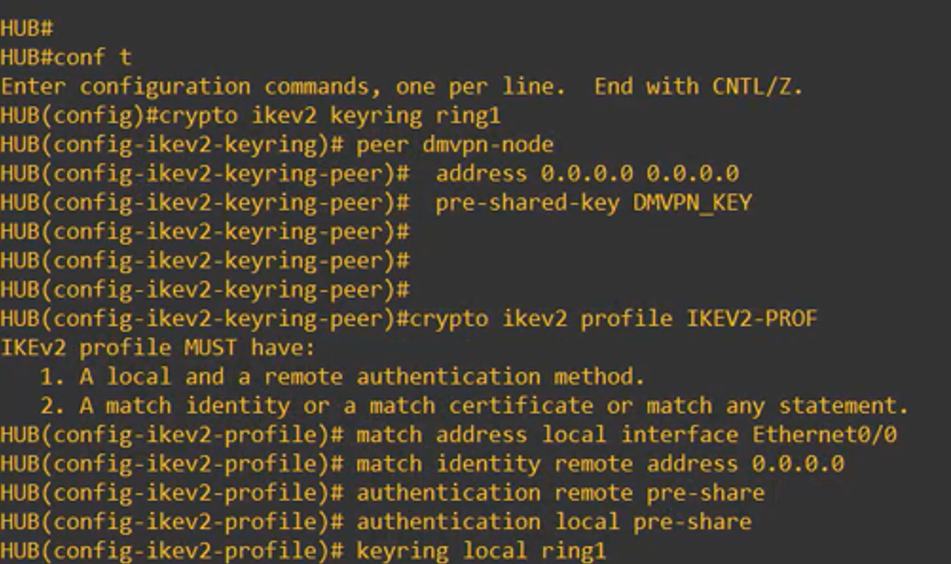
Enter configuration mode and use the following commands to define the IKEv2 keyring and the IKEv2 profile.
The profile will include the pre-shared key and a reference to the keyring.
Below is the expected output you will see on the router while configuring this section:
Then, set the IPsec profile linking it tot he IKEv2 phase 1 profile:
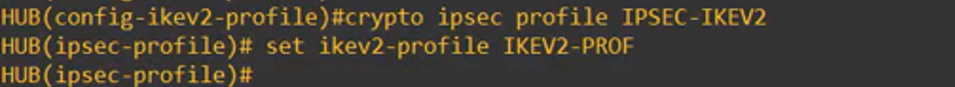
The resulting configuration will be:
crypto ikev2 keyring ring1
peer dmvpn-node
address 0.0.0.0 0.0.0.0
pre-shared-key DMVPN_KE
crypto ikev2 profile IKEV2-PROF
match address local interface Ethernet0/0
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local ring1
crypto ipsec profile IPSEC-IKEV2
set ikev2-profile IKEV2-PROF
3. Tunnel Interface Configuration (mGRE)
- Create and Configure the Tunnel Interface: add a new tunnel interface and assign it an IP address using a /24 subnet mask. This subnet size is necessary because the tunnel will operate in multipoint GRE (mGRE) mode.
- Set Tunnel Source and Mode: Define the tunnel source, which can be either a physical interface or a specific IP address on the router. Then, configure the tunnel mode to gre multipoint to support multiple GRE peers over a single logical interface, which is essential for DMVPN.
- Apply IPsec Protection: To secure the GRE traffic, apply an IPsec protection profile to the tunnel interface.
- Adjust MTU Settings to 1400: this is important to prevent fragmentation issues caused by the additional overhead introduced by GRE and IPsec headers.
Below is the expected output you will see on the router while configuring this section:
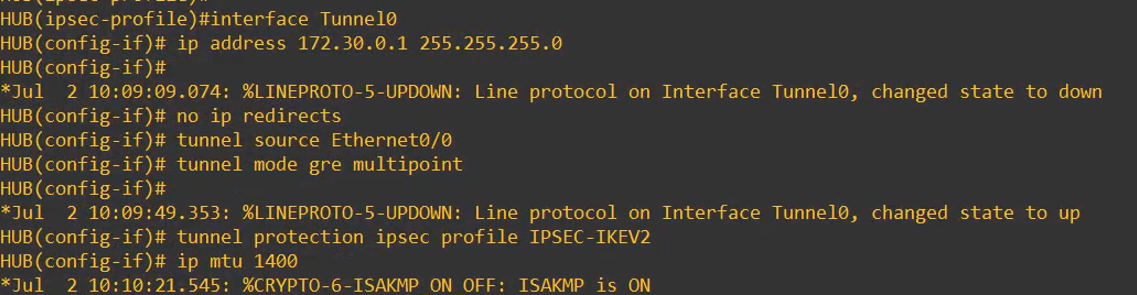
The resulting configuration will be:
interface Tunnel0
ip address 172.30.0.1 255.255.255.0
no ip redirects
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel protection ipsec profile IPSEC-IKEV2
ip mtu 1400
4. NHRP Configuration
Since this is the central (HQ) router, we also configure NHRP (Next Hop Resolution Protocol) under the Tunnel interface:
- Enable dynamic multicast mapping
- Set a network ID, which must match across all routers in the DMVPN network
- Enable NHRP redirect, which is required on the hub router to support spoke-to-spoke communication
Below is the expected output you will see on the router while configuring this section:

The resulting configuration will be:
interface Tunnel0
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp redirect
5. BGP Configuration
All routers in this network will participate in iBGP using the same Autonomous System Number (ASN 65101):
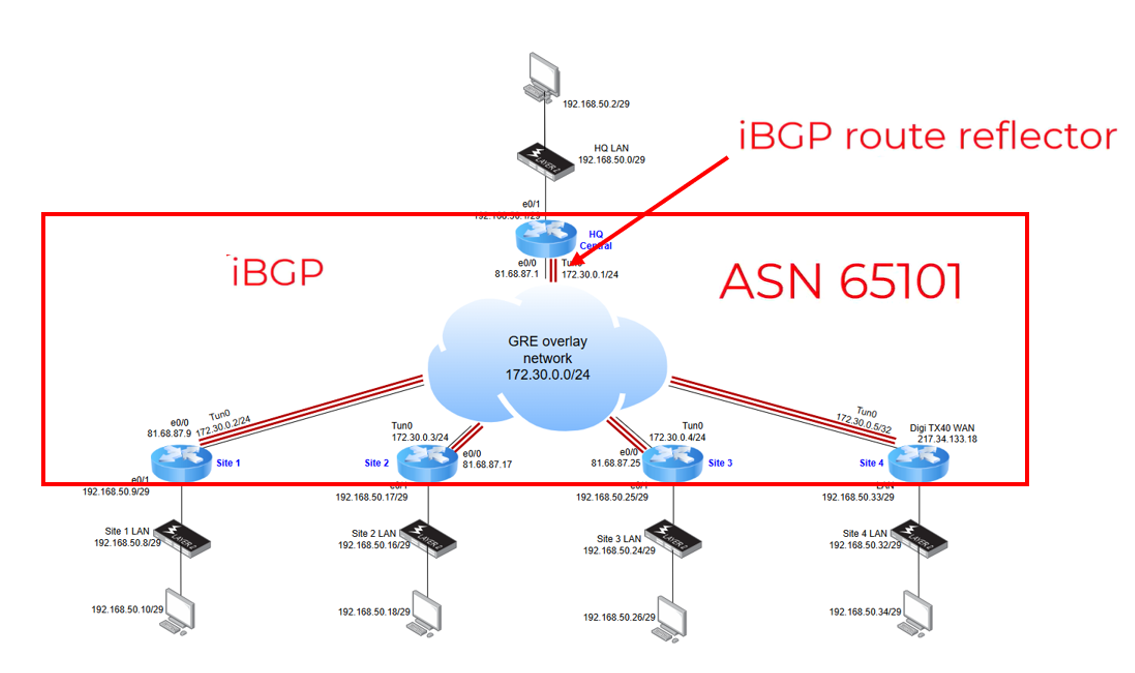
On the HQ router, the following configurations must be applied:
- Enable BGP with ASN 65101.
- Set the router ID to the IP address of the Tunnel interface.
- Advertise the LAN network using the network command.
- Enable log-neighbor-changes to monitor BGP session status changes.
- Configure BGP timers, including the update interval and hold time.
- For each remote site (iBGP peer):
- Configure the neighbor with the same ASN (65101)
- Mark each neighbor as a route-reflector-client.
This setup allows the HQ router to act as a Route Reflector, ensuring that any routes received from one iBGP peer are reflected to all other iBGP peers.
Below is the expected output you will see on the router while configuring this section:
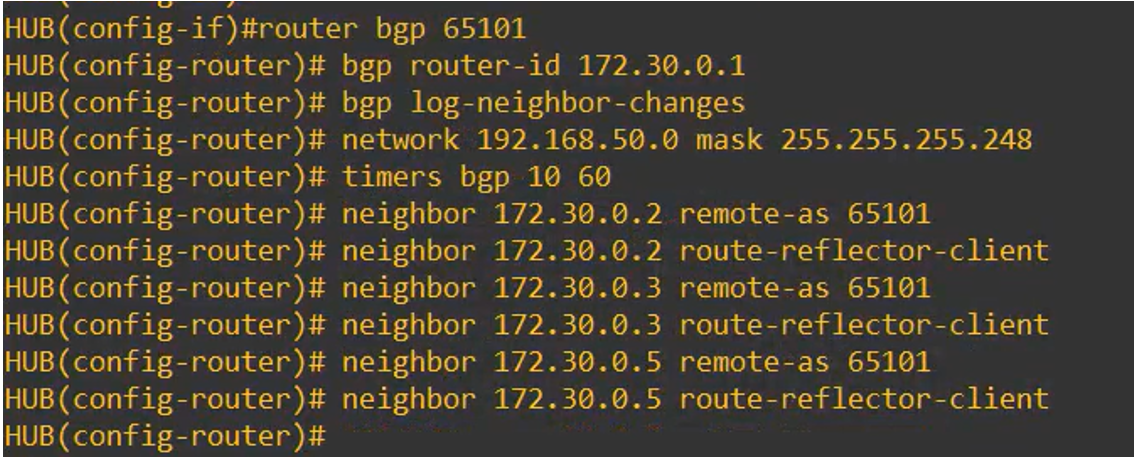
The resulting configuration will be:
router bgp 65101
bgp router-id 172.30.0.1
bgp log-neighbor-changes
network 192.168.50.0 mask 255.255.255.248
timers bgp 10 60
neighbor 172.30.0.2 remote-as 65101
neighbor 172.30.0.2 route-reflector-client
neighbor 172.30.0.3 remote-as 65101
neighbor 172.30.0.3 route-reflector-client
neighbor 172.30.0.5 remote-as-65101
neighbor-172,30.0.5 route-reflector-client
6. Complete DMVPN Cisco HUB configuration:
To finalize the setup, make sure to save the configuration so that all changes persist after a reboot:
Below is the complete DMVPN configuration applied to the Central Cisco HUB router:
interface Tunnel0
crypto ikev2 keyring
peer dmvpn-node
address 0.0.0.0 0.0.0.0
pre-shared-key DMVPN_KEY
!
crypto ikev2 profile IKEV2-PROF
match address local interface Ethernet0/0
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local ring1
!
crypto ipsec profile IPSEC-IKEV2
set ikev2-profile IKEV2-PROF
!
ip address 172.30.0.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp redirect
tunnel source Ethernet0/0
tunnel mode gre multipoint
tunnel protection ipsec profile IPSEC-IKEV2
!
interface Ethernet0/0
ip address 81.68.87.1 255.255.255.248
ip nat outside
ip virtual-reassembly in
!
interface Ethernet0/1
ip address 192.168.50.1 255.255.255.248
ip nat inside
ip virtual-reassembly in
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
router bgp 65101
bgp router-id 172.30.0.1
bgp log-neighbor-changes
network 192.168.50.0 mask 255.255.255.248
timers bgp 60 180
neighbor 10.0.0.2 remote-as 65102
neighbor 10.0.0.2 route-reflector-client
neighbor 10.0.0.3 remote-as 65103
neighbor 10.0.0.3 route-reflector-client
neighbor 10.0.0.4 remote-as 65104
neighbor 10.0.0.4 route-reflector-client
!
Further Information
Related Video: [link]
Next KB of the series: [link to part3]
Introduction and KB/Video Index: [link to KB - 0 that contains all video/kb list and links]
Last updated:
Jul 08, 2025