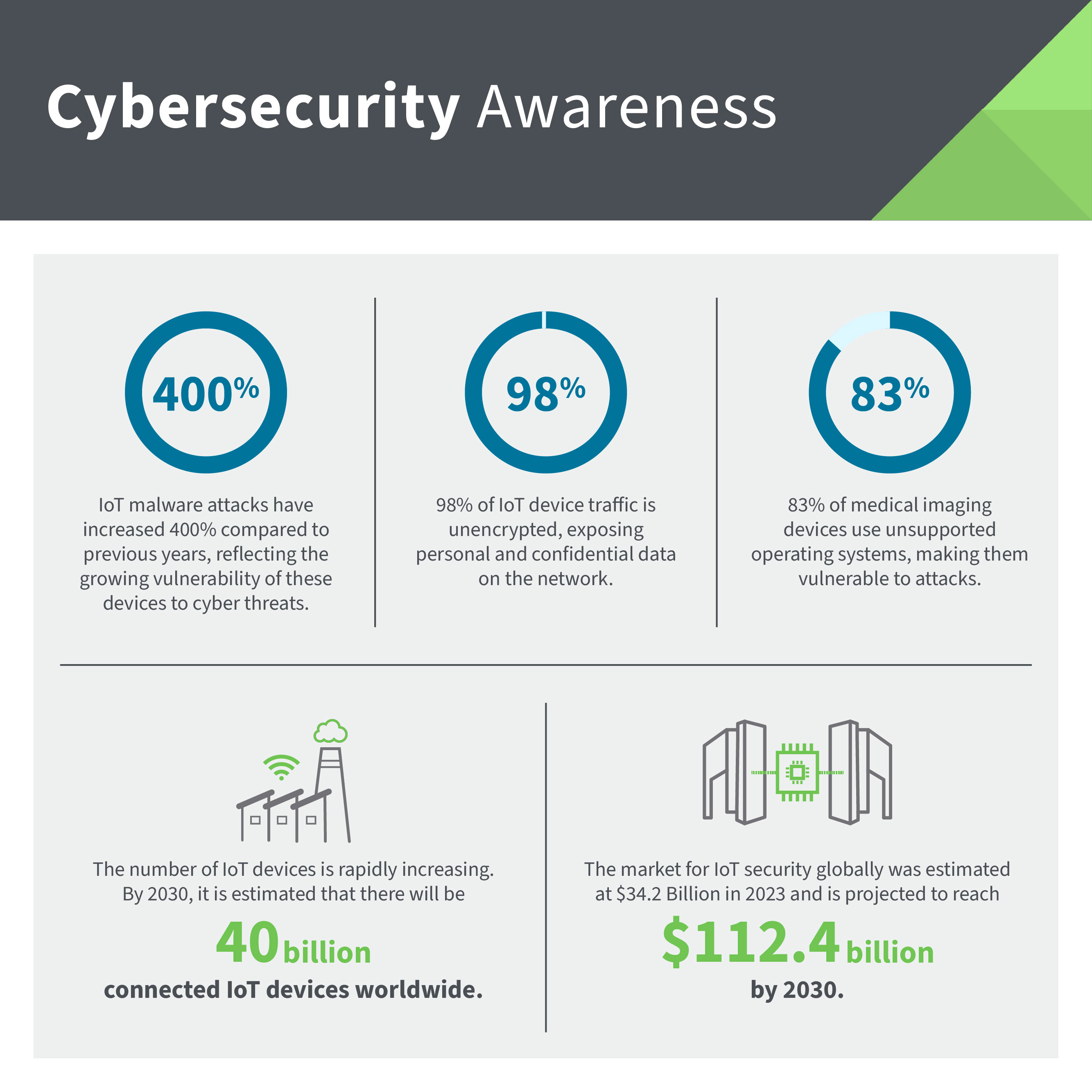
Billions of connected devices power homes, businesses, and industries, but IoT security remains a growing concern. By 2030, experts predict over
40 billion IoT devices worldwide, creating vast opportunities — and serious risks. Cybercriminals constantly attempt to exploit weak points in smart devices, leading to data breaches, system takeovers, and real-world disruptions.
Security in the Internet of Things requires a proactive approach, from strong encryption to secure device management. Companies that fail to protect their IoT ecosystems risk costly attacks and reputational damage. And OEMs today are facing increasing scrutiny and requirements around long-term lifecycle security and management of the devices they bring to market. Digi delivers trusted IoT security solutions, helping businesses safeguard their networks and stay ahead of emerging threats in an increasingly connected world.
What Is IoT Security?

What is IoT security? It’s the practice of protecting connected devices, networks, and data from cyber threats. Today, even with more awareness of the risks, cybersecurity threats are trending upward. And it's not just IT teams that need to be diligent — it’s everyone’s responsibility. Today, businesses and consumers alike rely on connected systems for automation, efficiency, and real-time insights, which means strong security measures are essential.
IoT device security involves encryption, secure authentication, firmware updates, and network monitoring to prevent unauthorized access and data breaches. Without these safeguards, attackers can exploit vulnerabilities, disrupt operations, and steal sensitive information.
Companies must proactively integrate security protocols at every level, from device manufacturing to data transmission. A well-protected IoT ecosystem ensures reliability, prevents downtime, and builds trust in connected technology. As threats evolve, organizations need robust, adaptive security strategies to defend against emerging risks in an interconnected world.
Why Securing the IoT Is Important
 Securing the IoT is crucial because cybercriminals constantly seek to exploit weaknesses in connected devices. As more industries integrate IoT technology, the risk of data breaches, financial losses, and operational disruptions increases.
Securing the IoT is crucial because cybercriminals constantly seek to exploit weaknesses in connected devices. As more industries integrate IoT technology, the risk of data breaches, financial losses, and operational disruptions increases.
A single vulnerability in an industrial sensor, smart home system, or healthcare device can compromise sensitive data, leading to severe consequences. Internet of Things device security protects against hacking, unauthorized access, and malware attacks that could hobble businesses and expose consumer information.
The growing number of connected devices makes security a top priority for enterprises and individuals alike. By implementing strong authentication, encryption, and network segmentation, organizations can safeguard their IoT ecosystems and prevent costly cyber incidents that threaten safety, privacy, and business continuity.
Economic and Operational Impacts of IoT Security Breaches
 IoT security breaches can cause financial losses, legal penalties, and operational chaos. A cyberattack on an industrial IoT system can halt production, while a data breach in healthcare IoT can expose patient records, leading to lawsuits.
IoT security breaches can cause financial losses, legal penalties, and operational chaos. A cyberattack on an industrial IoT system can halt production, while a data breach in healthcare IoT can expose patient records, leading to lawsuits.
In 2023, cyber security incidents of all types — including those involving IoT devices — cost businesses an estimated $10.5 trillion globally.
Consequences of IoT security failures include:
- Revenue loss from operational downtime
- Fines for non-compliance with data regulations
- Reputational damage and loss of customer trust
- Intellectual property theft impacting competitiveness
- Increased costs for remediation and cybersecurity upgrades
Organizations must prioritize proactive security measures to avoid these costly disruptions and maintain a resilient IoT infrastructure.
Widespread adoption and integration across industries increase Internet-connected devices security risks. From smart home assistants to industrial sensors, each device presents a potential entry point for cybercriminals.
Unpatched vulnerabilities, weak authentication, and insecure data transmission create serious threats. Hackers can exploit these gaps to launch ransomware attacks, steal data, or manipulate systems.
Securing the Internet of Things requires a layered defense strategy, ensuring encryption, regular updates, and network segmentation. As IoT expands, businesses and consumers must stay vigilant, recognizing risks before they escalate into major security incidents. Strengthening device security prevents costly breaches and protects critical infrastructure from cyber threats.

IoT Sensors
IoT sensors collect and transmit real-time data across industries, from healthcare to manufacturing. However, these devices often lack built-in security, making them vulnerable to cyber threats.
Attackers can manipulate sensor data, causing inaccurate readings in industrial processes or patient monitoring systems. IoT security risks increase when sensors connect to unprotected networks, allowing hackers to intercept or alter information. Weak authentication protocols and outdated firmware make them easy targets for cybercriminals.
A compromised sensor can disrupt entire IoT ecosystems, leading to financial losses, safety concerns, and operational downtime. Regular software updates and encrypted data transmission help mitigate these risks.
Wearables and Smart Home Devices
Wearables and smart home devices enhance convenience but introduce significant Internet of Things security risks. Weak encryption, poor password management, and insecure cloud connections expose user data to cyber threats. Hackers can exploit these vulnerabilities to gain access to sensitive health information or hijack smart home systems.
A compromised wearable may leak biometric data, while a hacked security camera can serve as an entry point into home networks. These risks extend beyond individual users, affecting broader IoT ecosystems. Strengthening authentication protocols, securing cloud storage, and regularly updating firmware help mitigate these threats, ensuring privacy and device integrity.
Connected Vehicles and Drones
Connected vehicles and drones rely on wireless communication, making them prime cyberattack targets. Hackers can exploit weak authentication to take control of a vehicle’s navigation or disable safety features, endangering passengers and pedestrians. Drones for deliveries or surveillance are potentially vulnerable to hijacking, leading to stolen payloads or compromised security operations.
The security of IoT devices in transportation requires encryption, real-time monitoring, and firmware updates to prevent unauthorized access. Without proper safeguards, attackers can manipulate GPS signals, interfere with fleet management systems, and disrupt logistics networks. Strengthening cybersecurity in connected transportation ensures safe, reliable operations.
Edge Computing Devices
Edge computing devices process data closer to the source, reducing latency and improving efficiency. However, their decentralized nature makes them vulnerable to cyber threats.
Without centralized oversight into these connected devices, hackers can exploit weak security protocols to access sensitive information or disrupt data flow. IoT attacks examples include man-in-the-middle attacks, where malicious actors intercept and alter data, and denial-of-service attacks that overwhelm systems with traffic.
Edge devices in healthcare, manufacturing, and smart cities must implement strong encryption, access controls, and real-time threat detection. Without these safeguards, cybercriminals can manipulate critical operations, leading to financial losses and compromised safety.
Industries that heavily rely on IoT technology face significant security risks. Healthcare, manufacturing, critical infrastructure, and smart cities have seen major breaches due to weak security measures and increasing cyber threats.
Hackers exploit vulnerabilities to steal data, disrupt operations, and compromise safety. IoT security challenges include outdated software, unsecured networks, and lack of proper authentication.
Digi’s solutions help these industries strengthen security frameworks, ensuring reliable and safe IoT implementations.
Healthcare Facilities
Healthcare facilities depend on IoT devices for patient monitoring, medical imaging, and critical care. However, weak security protocols expose hospitals to ransomware attacks, data breaches, and device manipulation. Cybercriminals exploit vulnerabilities in connected medical devices to access sensitive patient records or disrupt hospital operations. The stakes are high — compromised systems can delay treatments and endanger lives.
- WannaCry Attack on NHS (2017): Ransomware infected hospital systems, locking patient records and disrupting healthcare services across the UK
- UHS Ransomware Attack (2020): A Ryuk ransomware attack disabled systems across 400 hospitals, causing delays in patient care
- Medtronic Pacemaker Vulnerability (2018): A security flaw in pacemaker software exposed patients to potential remote hacking threats
Security challenges for the Internet of Things in healthcare demand strict encryption, real-time monitoring, and timely software updates to prevent cyberattacks.
Get Our White Paper
Learn about emerging medical device cybersecurity regulations
Download PDF
Manufacturing and Critical Infrastructure
Manufacturing and critical infrastructure rely on IoT for automation, supply chain management, and system monitoring. Cyberattacks can disrupt operations, cause financial losses, and threaten public safety. Industrial IoT devices often lack strong security measures, making them easy targets for hackers.
- Triton Malware Attack (2017): Hackers targeted industrial safety systems, attempting to disable emergency shutdown functions at a Saudi petrochemical plant
- Colonial Pipeline Ransomware Attack (2021): A cyberattack shut down the largest fuel pipeline in the U.S., causing fuel shortages and economic disruption
- Norsk Hydro Cyberattack (2019): A ransomware attack forced a major aluminum producer to halt production, resulting in $75 million in damages
IoT security threats in manufacturing highlight the need for strong access controls, real-time threat detection, and robust cybersecurity policies. Strengthening IoT security architecture can prevent costly disruptions and safeguard critical industries.
Smart Cities
Smart cities integrate IoT for traffic management, public safety, and energy efficiency. However, the challenges of securing IoT devices often leave these systems vulnerable to cyberattacks that can disrupt essential services, endanger citizens, and expose sensitive data.
- Dallas Emergency Siren Hack (2017): Hackers triggered all 156 tornado sirens, causing public panic and emergency response confusion.
- San Francisco Muni Ransomware Attack (2016): Hackers disabled ticket machines and forced the transit system to provide free rides.
- Mirai Botnet Attack (2016): In 2016, the Mirai malware infected numerous IoT devices, such as IP cameras and routers, by exploiting default credentials. This led to a massive distributed denial-of-service (DDoS) attack that disrupted major internet services, highlighting vulnerabilities in smart city infrastructures.
IoT security examples in smart cities show how cyberattacks can compromise safety and essential services. Strengthening network security, encryption, and authentication can mitigate risks.
Connected Transportation
Connected vehicles and smart transportation systems enhance efficiency but also introduce IoT security concerns. Hackers can exploit vulnerabilities to take control of vehicles, disrupt navigation systems, or steal data.
- Jeep Cherokee Hack (2015): Security researchers remotely took control of a Jeep’s acceleration and brakes, exposing critical flaws in-vehicle software
- Tesla Model S Key Fob Hack (2018): Hackers cloned Tesla key fobs to unlock and steal vehicles
- Kia Vehicles Web Portal Vulnerability (2024): Security researchers discovered a vulnerability in Kia's web portal that allowed them to reassign control of internet-connected features of Kia vehicles manufactured after 2013
Securing transportation IoT systems requires encrypted communication, multi-factor authentication, and strict access controls to prevent cyber threats.
Smart Grids and Utilities
Utilities rely on IoT for energy distribution, grid management, and resource optimization. Security issues with the Internet of Things in this sector can lead to large-scale outages, economic damage, and public safety risks.
Strengthening cybersecurity in smart grids requires real-time threat monitoring, strict authentication protocols, and network segmentation to prevent widespread disruptions.
Stay Connected and Secure — Effortless IoT Management with Digi Remote Manager
Regulatory frameworks help businesses meet IoT security requirements, protecting devices and networks. Standards like GDPR and ISO/IEC 27001 establish protocols for data protection and risk management. Organizations use these frameworks to implement encryption, secure authentication, and continuous monitoring.
Digi solutions align with these standards by offering secure connectivity, device management, and real-time threat detection. Adhering to these guidelines strengthens security posture, reducing vulnerabilities and safeguarding IoT ecosystems from cyber threats.
Cyber Resilience Act (CRA), (EU) 2024/2847
On December 10, 2024, the Cyber Resilience Act regulation came into force. Any OEM around the world that plans to market their connected products in the EU must comply. The CRA significantly changes the EU product compliance landscape. It integrates stricter cybersecurity measures into the existing framework for CE marking. It is mandatory for any product or software that contains digital elements. Both manufacturers and distributors have responsibility throughout the entire product lifecycle. It addresses poor levels of cybersecurity in products or inadequate security updates, and how consumers and businesses can determine which products are secure or how to configure them to ensure their protection.
The Digi ConnectCore® ecosystem provides a broad range of secure-by-design building blocks, software, tools and services designed to facilitate CRA adoption and compliance, helping OEM customers build devices that comply with this legislation, reducing time to market and, more importantly, maintaining compliance from cradle to grave.
NISTIR 8259
The National Institute of Standards and Technology (NIST) developed NISTIR 8259 to provide IoT platform security guidelines. It outlines best practices for manufacturers to design secure IoT devices, emphasizing risk assessment, secure software development, and lifecycle management. Compliance helps organizations mitigate threats by implementing strong authentication, firmware integrity checks, and vulnerability reporting.
Digi solutions integrate these principles, offering robust security controls that align with NISTIR 8259’s recommendations, ensuring reliable and resilient IoT infrastructures.
ETSI EN 303 645
ETSI EN 303 645 sets IoT device security benchmarks in Europe, ensuring manufacturers follow best practices to prevent cyberattacks. This standard requires devices to use unique credentials, encrypt sensitive data, and receive software updates throughout their lifecycle. It also emphasizes secure communication protocols and incident reporting mechanisms. By complying with ETSI EN 303 645, companies enhance consumer trust and reduce the risk of breaches.
Digi supports these requirements by offering end-to-end security solutions tailored for IoT environments.
IoT Cybersecurity Improvement Act
The IoT Cybersecurity Improvement Act mandates strict security guidelines for government-purchased IoT devices in the U.S. It requires manufacturers to meet baseline security standards, such as vulnerability disclosure programs, secure software development, and compliance with NIST guidelines. This law ensures government agencies only deploy secure IoT solutions, reducing the risk of cyber threats.
Organizations looking to align with these regulations can benefit from Digi’s security-focused IoT solutions, which incorporate encryption, access controls, and continuous monitoring.
UL 2900-1 Certification
UL 2900-1 Certification establishes IoT network security standards for connected devices across industries. It evaluates products based on software vulnerabilities, malware protection, and encryption strength. Devices must undergo rigorous testing to ensure they meet security and privacy requirements. Achieving this certification demonstrates a commitment to cybersecurity, reducing risks associated with IoT deployments.
Digi incorporates UL 2900-1 principles into its solutions, helping businesses secure their IoT networks against cyber threats while maintaining compliance with industry standards.
Organizations struggle with securing IoT systems due to their complexity, rapid expansion, and evolving threats. Unlike traditional IT environments, IoT ecosystems involve diverse devices with varying security capabilities, making standardization difficult.
Many connected devices lack built-in security, creating vulnerabilities that attackers can exploit. Resource constraints further complicate security efforts, as many organizations lack the budget, expertise, or personnel to implement robust protections.
Additionally, IoT security problems arise from the growing sophistication of cyber threats, including ransomware and botnets targeting unprotected devices. As attack surfaces expand, businesses must adopt strategic security measures like network segmentation, strong authentication, and continuous monitoring.
Without a proactive approach, organizations risk data breaches, operational disruptions, and regulatory penalties, emphasizing the critical need for comprehensive IoT security frameworks.
Common IoT Security Issues
IoT security issues create significant organizational risks, threatening data integrity, system functionality, and overall operational security. Many devices rely on weak authentication mechanisms, using default credentials or easily guessed passwords, making unauthorized access a serious concern.
Unsecured communication channels expose sensitive data, especially when devices transmit information over unencrypted networks or outdated protocols. Insufficient patch management leaves IoT systems vulnerable, as many devices do not receive regular updates or security fixes, allowing attackers to exploit known weaknesses. Vulnerable APIs present another challenge, as poorly secured interfaces can give attackers a direct entry point into critical systems.
These security flaws increase the likelihood of cyberattacks, making it essential for organizations to implement robust security protocols and proactive risk management strategies to protect their IoT infrastructure.

Securing IoT systems requires a strong foundation of essential protections to mitigate cyber threats.
Device authentication ensures that only authorized devices access networks, preventing malicious intrusions. Data encryption safeguards sensitive information during transmission and storage, reducing exposure to breaches. Firmware updates and patches address vulnerabilities, keeping devices protected against emerging threats. Role-based access control (RBAC) restricts system access based on user roles, minimizing risks from unauthorized users. Incident response planning prepares organizations to detect, contain, and recover from cyberattacks effectively.
These IoT security requirements establish a resilient defense against evolving threats, reducing risks associated with unauthorized access, data leaks, and operational disruptions. Implementing these core measures strengthens IoT ecosystems and ensures long-term security and compliance.
Device Authentication
Strong authentication prevents unauthorized devices from accessing networks, ensuring only verified IoT endpoints communicate within an ecosystem. Without this safeguard, attackers can infiltrate systems, manipulate data, or disrupt operations.
Securing IoT devices with robust authentication methods — such as digital certificates or multi-factor authentication — prevents identity spoofing and unauthorized access. As IoT networks expand, authentication ensures a trustworthy environment, reducing the risk of compromised endpoints introducing security threats.
Organizations that prioritize authentication can maintain data integrity, system reliability, and regulatory compliance, reinforcing overall security.
Data Encryption
Encryption protects sensitive data as it moves across IoT networks, making it unreadable to unauthorized users. Without it, hackers can intercept transmissions and extract critical information.
Security solutions for IoT must include end-to-end encryption to prevent data leaks, whether in transit or at rest. Strong encryption protocols — such as AES or TLS — ensure confidentiality, protecting everything from personal health data to industrial control system commands.
Organizations that implement encryption reduce their risk of cyberattacks, enhance consumer trust, and comply with global security regulations.
Firmware Updates and Patches
IoT devices require regular firmware updates to fix vulnerabilities and strengthen defenses against cyber threats. Without consistent patching, attackers can exploit outdated software, compromising entire networks.
IoT security depends on manufacturers and users deploying security patches promptly to address newly discovered weaknesses. Automated update mechanisms help ensure devices stay protected without requiring manual intervention.
Organizations that prioritize firmware maintenance reduce their exposure to cyber risks, prevent unauthorized control of IoT systems, and uphold data security standards. Keeping devices updated enhances reliability and long-term protection.
Role-Based Access Control (RBAC)
RBAC restricts system access based on user roles, minimizing unauthorized interactions with IoT devices and sensitive data. Internet of Things security solutions must include access control measures to ensure that only authorized personnel can modify configurations, retrieve data, or execute commands.
By limiting user permissions according to job functions, organizations prevent insider threats and accidental misconfigurations. Implementing RBAC enhances overall security posture, reduces attack surfaces, and ensures compliance with data protection regulations.
Organizations that enforce strict access controls strengthen IoT security and reduce operational risks.
Incident Response Planning
A well-defined incident response strategy prepares organizations to detect, contain, and recover from cyber threats targeting IoT systems. Without a plan, security breaches can escalate, causing prolonged downtime and financial losses.
A strong incident response framework includes real-time threat detection, rapid containment measures, and clear recovery protocols. Organizations must also conduct regular simulations to refine their response capabilities. Proactive planning ensures minimal disruption when attacks occur, strengthening resilience and maintaining business continuity in the face of evolving cyber threats.
Securing IoT devices requires a multi-layered approach combining proactive defense strategies and strong security frameworks. Organizations must implement device authentication, network segmentation, and encryption to protect sensitive data.
Regular software updates and robust access control policies reduce risks from emerging threats. Establishing clear incident response procedures ensures rapid mitigation when attacks occur.
By adopting these best practices, businesses strengthen their IoT security posture, minimizing vulnerabilities while maintaining operational efficiency and data integrity. Proactive security measures create resilient, trustworthy IoT ecosystems.

Implement a Zero-Trust Architecture
Zero-trust security ensures that every device, user, and network request undergoes strict verification before gaining access. This approach protects against unauthorized access, lateral movement attacks, and insider threats.
Organizations must enforce least-privilege access, continuous authentication, and segmentation to reduce exposure. IoT security architecture benefits from a zero-trust framework by eliminating blind spots and securing sensitive data at every interaction point.
- Enforce continuous authentication and authorization for all network interactions
- Apply micro-segmentation to isolate critical systems and limit exposure
- Implement context-aware access controls that adapt to real-time security conditions
Segment IoT Networks
Segmenting networks prevents IoT vulnerabilities from affecting broader infrastructure. Creating isolated network zones limits unauthorized access and prevents attackers from moving between systems.
Organizations should implement strong network policies that control communication between segments. IoT network security benefits from segmentation by containing potential threats and reducing attack surfaces.
- Establish VLANs to separate IoT traffic from core business systems
- Use firewalls and ACLs to control and monitor data exchange between segments
- Continuously analyze inter-segment traffic to detect unusual behaviors or threats
Onboard Devices Securely
A secure onboarding process prevents compromised or rogue devices from infiltrating IoT ecosystems. Organizations must implement authentication and validation steps to verify device integrity before deployment. IoT platform security improves when businesses ensure each device follows strict provisioning and configuration policies.
- Assign unique cryptographic keys or digital certificates for secure authentication
- Enforce strong, unique credentials to replace factory-default passwords
- Utilize secure boot processes to validate firmware and system integrity
Strengthen Data Encryption
Strong encryption safeguards sensitive data in IoT systems from unauthorized access and tampering. Organizations should adopt advanced cryptographic techniques to secure data transmission and storage.
Implementing encryption ensures compliance with industry standards while mitigating the risks of breaches. IoT security depends on encrypted communications to maintain confidentiality.
- Deploy AES-256 or ECC for robust encryption
- Secure sensitive data with TLS 1.3 or VPN tunneling protocols
- Rotate encryption keys periodically to mitigate potential compromises
Leverage Threat Detection and Monitoring Tools
Proactive threat detection identifies and mitigates security incidents before they escalate. AI-powered monitoring tools analyze network activity, detect anomalies, and provide real-time alerts.
Organizations must integrate automated defenses to protect IoT infrastructures from evolving threats. Essentially, continuous surveillance effectively minimizes IoT security threats.
- Deploy AI-driven IDS/IPS to analyze network traffic and detect intrusions
- Use SIEM tools to aggregate and respond to security events across IoT networks
- Implement behavioral analytics to flag abnormal device activity
Practice Data Minimization
Minimizing data collection reduces exposure to breaches while ensuring compliance with privacy regulations. IoT systems should only store essential information, preventing unnecessary risks.
Organizations must establish clear policies to limit data storage and optimize retention. Often, mitigating IoT security challenges by reducing the volume of sensitive information is a straightforward strategy.
- Collect only the minimum data required for IoT functionality
- Avoid storing redundant or unnecessary information on IoT devices
- Regularly review and optimize data retention policies to align with security best practices
Limit Third-Party Integrations
Third-party services introduce potential security vulnerabilities that can compromise IoT networks. Organizations should vet external vendors and enforce strict security policies for integrations. IoT cyber security improves when businesses minimize reliance on unverified third-party solutions.
- Restrict integrations to trusted vendors with proven security standards
- Use sandbox environments to test third-party APIs before full deployment
- Conduct regular audits of third-party services to identify vulnerabilities
Use Blockchain for Device and Data Security
Blockchain technology enhances IoT security by providing decentralized and tamper-resistant transaction records. Organizations can implement blockchain for secure authentication, data validation, and automated device interactions. Securing IoT devices with blockchain prevents data manipulation and strengthens overall network integrity.
- Use blockchain to assign immutable identities for IoT devices
- Leverage smart contracts for automated and secure data transactions
- Ensure data integrity across decentralized IoT networks
Implement Hardware Root of Trust
Hardware root of trust enhances security at the device level by embedding cryptographic functions in IoT hardware. Organizations must ensure devices can authenticate securely and prevent unauthorized modifications. IoT network security benefits from hardware-based trust mechanisms that provide verifiable identity protection.
- Use hardware-backed encryption for secure device identity authentication
- Establish tamper-proof mechanisms to detect unauthorized changes
- Enable secure boot to validate firmware integrity before system startup
Establish Incident Response Plans
A well-defined incident response strategy ensures rapid mitigation of security incidents. Organizations must develop structured playbooks for handling IoT attacks and conduct regular simulations to improve preparedness. IoT security risks decrease when businesses proactively respond to threats.
- Define clear roles and responsibilities for incident response teams
- Develop attack-specific playbooks for threats like ransomware and DDoS attacks
- Conduct periodic response drills to refine recovery strategies
Train and Empower Teams
Educating teams on IoT security protocols strengthens an organization’s overall defense posture. Employees should understand security best practices, recognize potential threats, and follow standardized protocols. IoT security improves when organizations invest in continuous education.
- Conduct security awareness training tailored to IoT-specific risks
- Establish clear policies on device usage, maintenance, and software updates
- Encourage employees to report anomalies or suspicious activities immediately
Robust security compliance ensures IoT systems remain resilient against evolving cyber threats. Developers and designers must integrate strong authentication, encryption, and real-time monitoring to protect devices and networks. Implementing proactive security frameworks prevents unauthorized access and data breaches.
Digi offers industry-leading solutions — like Zigbee 3.0 security — tailored to diverse IoT security needs, from smart cities to industrial automation. Explore Digi’s advanced security tools to enhance device protection, maintain compliance, and secure your IoT infrastructure. Strengthen your security strategy with Digi’s expertise and innovative solutions for long-term device protection.
Smart City IoT Security Solutions
Smart city security depends on reliable, high-bandwidth wireless connectivity.
Digi’s solutions empower security professionals with real-time video streaming from drones, cameras, and sensors, ensuring instant situational awareness. Remote alarm monitoring minimizes unnecessary site visits and prevents false law enforcement dispatches. Users can seamlessly interact with security systems via mobile devices, receiving alerts and exercising remote control over their smart city infrastructures.
Digi TrustFence, a Security Framework for IoT Devices
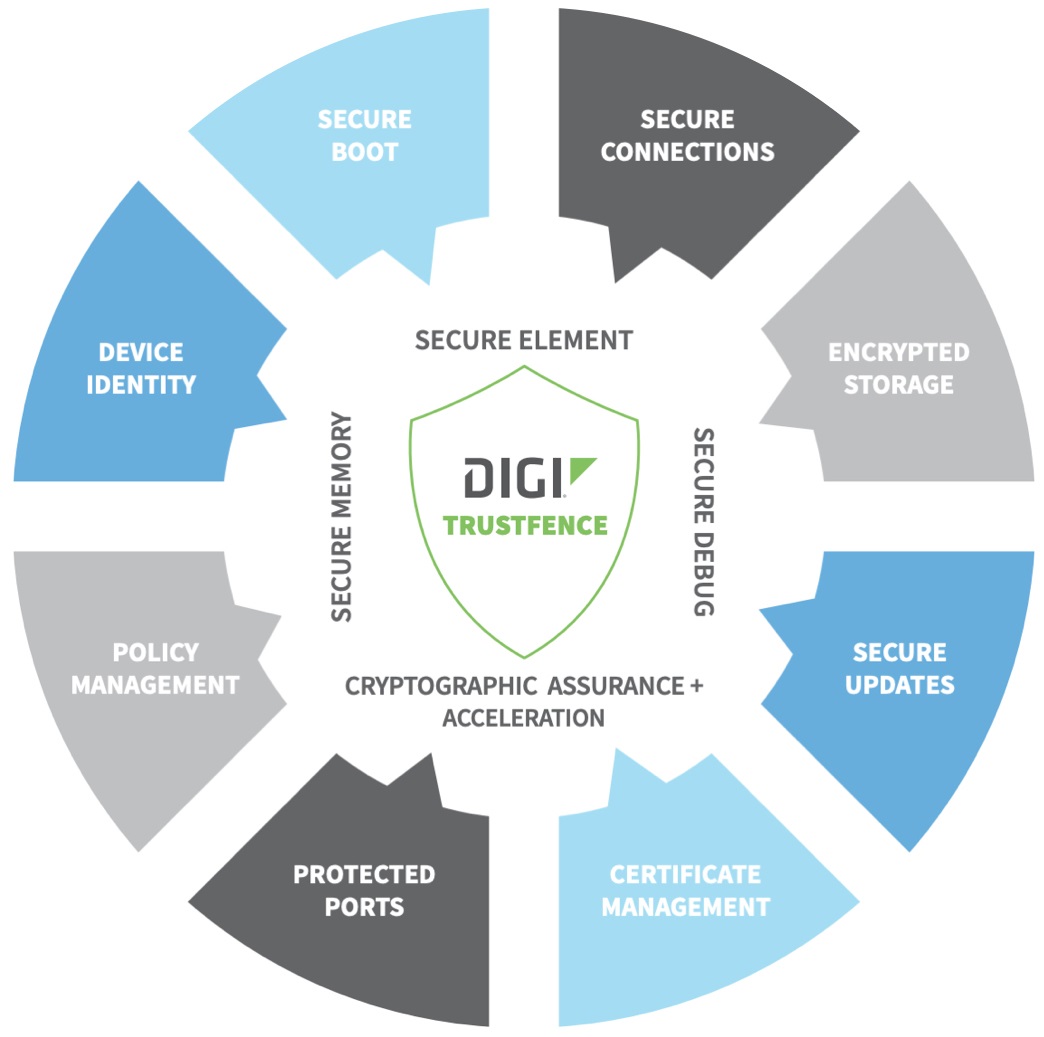 Digi TrustFence® enhances IoT security by integrating ready-to-use features such as secure boot, secure firmware updates, encrypted file system, and tamper detection. Secure boot validation ensures that only authorized code runs on devices. Hardened hardware and network ports prevent unauthorized access, while network authentication strengthens device identity management.
Digi TrustFence® enhances IoT security by integrating ready-to-use features such as secure boot, secure firmware updates, encrypted file system, and tamper detection. Secure boot validation ensures that only authorized code runs on devices. Hardened hardware and network ports prevent unauthorized access, while network authentication strengthens device identity management.
Digi TrustFence offers security by design, enhancing security from deployment. Encrypted file system protects data integrity, and tamper detection provides a mechanism to detect unauthorized attempts to access the system such as the opening of the enclosure, making Digi TrustFence a reliable framework for securing IoT ecosystems.
 Digi ConnectCore Security Services, supporting OEMs in safeguarding IoT devices throughout their lifecycle. These security services provide vulnerability tracking, curated vulnerability reports highlighting critical issues, and a security software layer for effective threat mitigation.
Digi ConnectCore Security Services, supporting OEMs in safeguarding IoT devices throughout their lifecycle. These security services provide vulnerability tracking, curated vulnerability reports highlighting critical issues, and a security software layer for effective threat mitigation.
OEM customers receive expert consulting and support services for patches and fixes integration for their Digi ConnectCore-based systems. Developers leveraging Digi ConnectCore benefit from enhanced security tools, ensuring their embedded systems remain protected against evolving cyber threats.
 Digi ConnectCore Cloud Services support security maintenance, offering secure and reliable remote over-the-air (OTA) software updates, and enabling process automation, monitoring, remote device management and cost reduction.
Digi ConnectCore Cloud Services support security maintenance, offering secure and reliable remote over-the-air (OTA) software updates, and enabling process automation, monitoring, remote device management and cost reduction.
Digi ConnectCore Cloud Services also provide mechanisms to securely distribute product updates to ensure that vulnerabilities are fixed or mitigated in a timely manner and, where applicable for security updates, in an automatic manner. Our cloud services ensure secure edge-to-cloud communications supporting TLS, certificate-based authentication and encryption.
Additionally, OEM device fleets can be automatically scanned, updated and maintained in compliance with the established configuration. By leveraging our cloud platform, OEM customers can save time, reduce errors, minimize effort, and manage scale when configuration updates are needed, as well as ensure consistency and standardization across all devices deployed in the field.
IoT Security FAQ

Why is IoT security important?
IoT devices often handle sensitive data and are integrated into critical systems such as healthcare, smart homes, manufacturing, and transportation. Due to their connectivity and often limited built-in protections, they are vulnerable to attacks. Poor security can lead to:
- Data breaches and privacy violations
- Botnet creation (e.g., Mirai)
- Disruption of services (DDoS attacks)
- Physical threats in industrial or medical settings
IoT security involves a secure-by-design approach, as well as integration of best practices during and after deployment, including proper encryption and authentication measures, physical device security and ongoing device monitoring and firmware updates over the product's lifecycle. Contact Digi to support your quest for secure connected solutions and services.
What are the most common IoT security risks?
The most common IoT security risks include:
- Weak/default passwords
- Unencrypted communication
- Outdated firmware/software
- Poor physical security
- Lack of network segmentation
- Unauthorized remote access
- Insecure APIs
Digi International is an industry leader in supporting secure, connected systems, with its integrated Digi TrustFence® security framework, secure-by-design embedded systems and connectivity solutions, and supporting services.
How can users secure their IoT devices?
Here are some best practices for end users:
- Change default credentials immediately after setup
- Regularly update firmware to patch known vulnerabilities
- Disable unnecessary services or features
- Enable encryption (e.g., TLS, VPN) for data transmission
- Use a separate network for IoT devices (e.g., guest Wi-Fi)
- Review privacy settings to limit data sharing
What should IoT manufacturers do to ensure security?
Manufacturers should implement security-by-design principles:
- Secure boot and hardware root of trust
- Encrypted firmware updates (OTA)
- Secure APIs and authentication mechanisms
- Lifecycle support for patches and security updates
- Compliance with standards and cybersecurity regulations such as NIST, ETSI EN 303 645, ISO/IEC 27400, and the Cyber Resilience Act
- Security testing throughout development and after deployment
Are there any regulations for IoT security?
Yes, IoT security regulations are increasing globally:
- U.S.: IoT Cybersecurity Improvement Act, NIST guidelines
- EU: Cyber Resilience Act (CRA), GDPR implications for data
- UK: Product Security and Telecommunications Infrastructure (PSTI) Act
- Global Standards: ETSI EN 303 645, ISO/IEC 27400, IEC 62443
These frameworks promote baseline security requirements for consumer and industrial IoT devices. Note that regulations affect products that are developed within those regions as well as products to be sold within those regions. For example, manufacturers that wish to put the CE mark on their products to be sold in the European Union must comply with the Cyber Resilience Act.
How does encryption protect IoT devices?
Encryption protects data at rest (stored on the device) and in transit (moving over the network). It ensures:
- Confidentiality: Only authorized parties can read the data
- Integrity: Prevents unauthorized modifications
- Authentication: Confirms the identity of devices or users
Common encryption tools include TLS/SSL, AES, and VPNs.
What is secure boot and why is it important?
Secure boot ensures a device only runs firmware that is digitally signed and verified. It protects against:
- Firmware tampering
- Malware injection during the boot process
- Running unauthorized third-party code
This is foundational for building a trusted IoT system.
Can IoT devices be updated remotely?
Yes, this method is known as an over-the-air (OTA) update. These updates are critical for ongoing maintenance of deployed devices, and this capability is an increasing requirement of OEMs via regulations such as the Cyber Resilience Act. Secure OTA systems must:
- Verify digital signatures of updates
- Use encrypted channels
- Maintain update logs and audit trails
- Avoid bricking devices during failure
Secure OTA capabilities help to ensure long-term protection against evolving threats.
What role does AI/ML play in IoT security?
AI and machine learning can:
- Detect anomalous behavior (intrusion detection)
- Identify zero-day threats
- Automate incident response
- Monitor device and network activity at scale
They’re especially useful for large-scale IoT deployments.
How do you test the security of an IoT device?
Security testing may include:
- Penetration testing
- Vulnerability scanning
- Fuzz testing of interfaces and protocols
- Threat modeling
- Code review and static analysis
Testing should occur during development and after deployment ─ over the entire product lifecycle.
What is Zero Trust in IoT?
Zero Trust means "never trust, always verify." Applied to IoT:
- Devices must authenticate before access
- Least-privilege access is enforced
- Continuous monitoring is required
- Assumes breaches are inevitable and contained
Zero Trust is becoming a key strategy in secure IoT networks.
Digi can support your organization in planning, designing and deploying secure IoT initiatives with the connected solutions, remote monitoring and management solutions, and services to help protect your organization, devices and data. Contact a Digi expert to get started.
Next Steps